Amazon EBS encryption offers a straight-forward encryption solution for your EBS resources that don’t require you to build, maintain, and secure your own key management infrastructure. It uses AWS Key Management Service (AWS KMS) customer master keys (CMK) when creating encrypted volumes and snapshots.
Encryption operations occur on the servers that host EC2 instances, ensuring the security of both data-at-rest and data-in-transit between an instance and its attached EBS storage.
About Nimesa
Nimesa is an enterprise-class Application Aware data protection, cost management & copy data management solution for applications running on AWS. It uses native AWS capabilities like EBS snapshots capabilities to automatically protect the environment. Nimesa provides simple policy based lifecycle management of snapshots and clones of EC2 instances.
You can encrypt both the boot and data volumes of an EC2 instance. When you create an encrypted EBS volume and attach it to a supported instance type, the following types of data are encrypted:
- Data at rest inside the volume
- All data moving between the volume and the instance
- All snapshots created from the volume
- All volumes created from those snapshots
EBS encrypts your volume with a data key using the industry-standard AES-256 algorithm. Your data key never appears on disk in plaintext. The same data key is shared by snapshots of the volume and any subsequent volumes created from those snapshots.
Pre-Requisite
For backup/restore/clone operations of the encrypted volumes in Nimesa, the registered IAM user should be added as Key user for the KMS key used for the encrypting the volume.
Read more on creating the IAM user for registering with Nimesa
Allows Key Users to Use the CMK
The default key policy that the console creates for symmetric CMKs allows you to choose IAM users and roles in the account, and external AWS accounts, and make them key users.
You can add IAM users, IAM roles, and other AWS accounts to the list of key users when you create the CMK.
Go to KMS > Customer managed keys
Choose your Customer managed key used for encrypting the volume and go to Key users section and click on Add and add the IAM user to the Key users

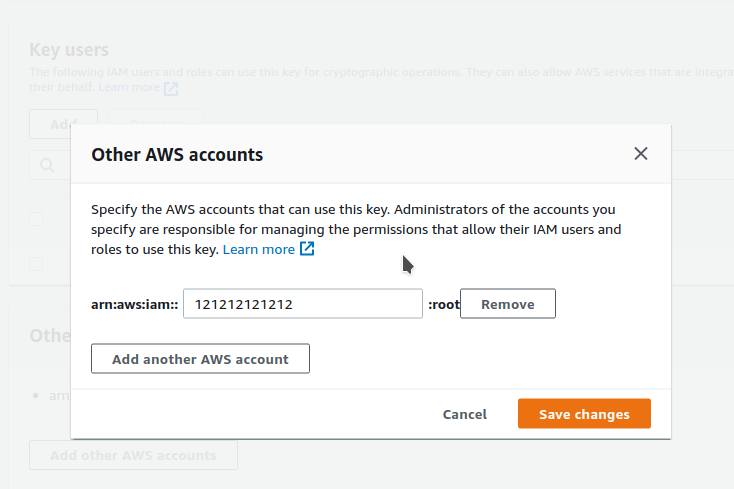
In the case of Cross Account DR
Go to KMS > Customer managed keys
Choose your Customer managed key used for encrypting the volume and go to Other AWS accounts section and add your AWS Account ID and save the changes
Once the IAM user is added as Key user, you can create the backup/restore/clone of the encrypted volumes using Nimesa
