Hancock Health CEO Steve Long said the hackers are believed to be in eastern Europe and may have used a type of ransomware called SamSam,
SamSam encrypted files and renamed them with the phrase “I’m sorry”, according to a local newspaper who broke the news.
The hospital said that despite having backups it opted to pay the ransom demand of 4 Bitcoin, which was worth around $55,000 at the time the hospital paid the sum. Hospital management told local press that restoring from backups was not a solution as it would have taken days and maybe even weeks to have all systems up and running. Hence, they decided to pay the ransom was quicker.
What is Ransomware
Ransomware is a type of malicious software from cryptovirology that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid. Ransomware is different from other attacks that it’s all about storage.
The hacker’s application locks up your storage by encrypting it and more advanced malware uses a technique called cryptoviral extortion, in which it encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them and you either unravel the rogue code’s encryption or start learning about blockchain technology and shipping bitcoins into the ether.
Today, ransomware is one of the biggest cyber threats, according to McAfee Labs and Trend Micro. Rapid digitization of consumers’ lives and enterprise records will increase the cost of data breaches drastically. To avoid becoming a victim, users take action to protect their Computers. But waiting ( RTO ) could cost you money, hassle, and negative publicity.
Backup admins should have periodic backups and good data protection with great RPOs and lesser RTOs to survive these attack
Protecting your data from Ransomware
In case of cloud environments ( VMware / AWS ) this is much easier to recover but many times a simple traditional backup app doesn’t provide sufficient defence against ransomware because those applications will backup only the application data of your machine.
Another big concern about ransomware is traditional backup stores their backup on the media server, as they would be susceptible to the same attacks that go after the systems they’re backing up.
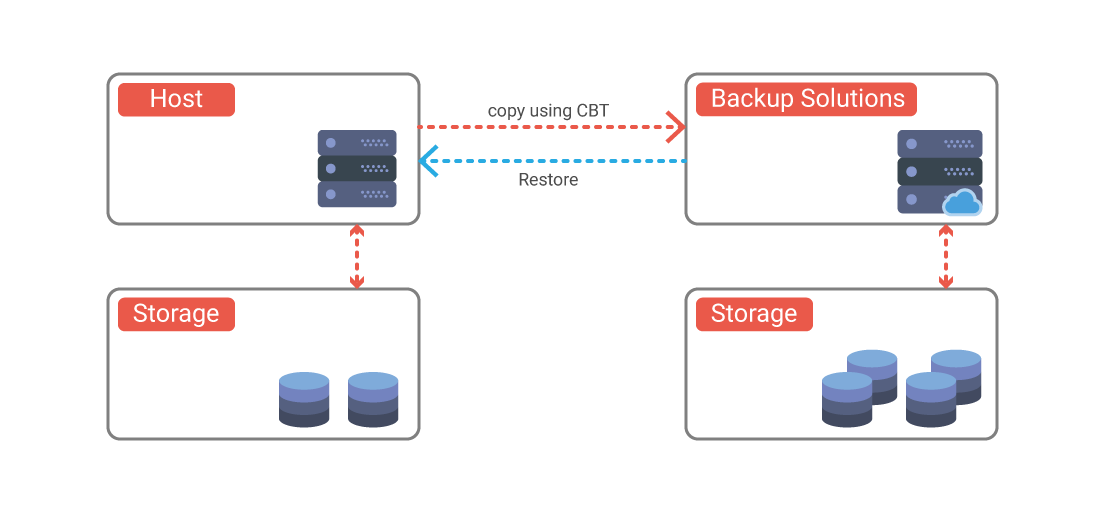
If you have a good copy of backup ( recovery point with the pre-ransomware copy of the data) you can recover your data but you still need everything related to operating system settings, application, application settings and the configurations to get up and run again in the production.
Is this sounds like it will take a lot of time to bring back production machine?
Introducing Nimesa
No, With Nimesa, A Best data protection technique which can help business by cloud-based disaster recovery, backup up data and replicate to another site. In case, ransomware blocks you on-prem data you can recover from another site.
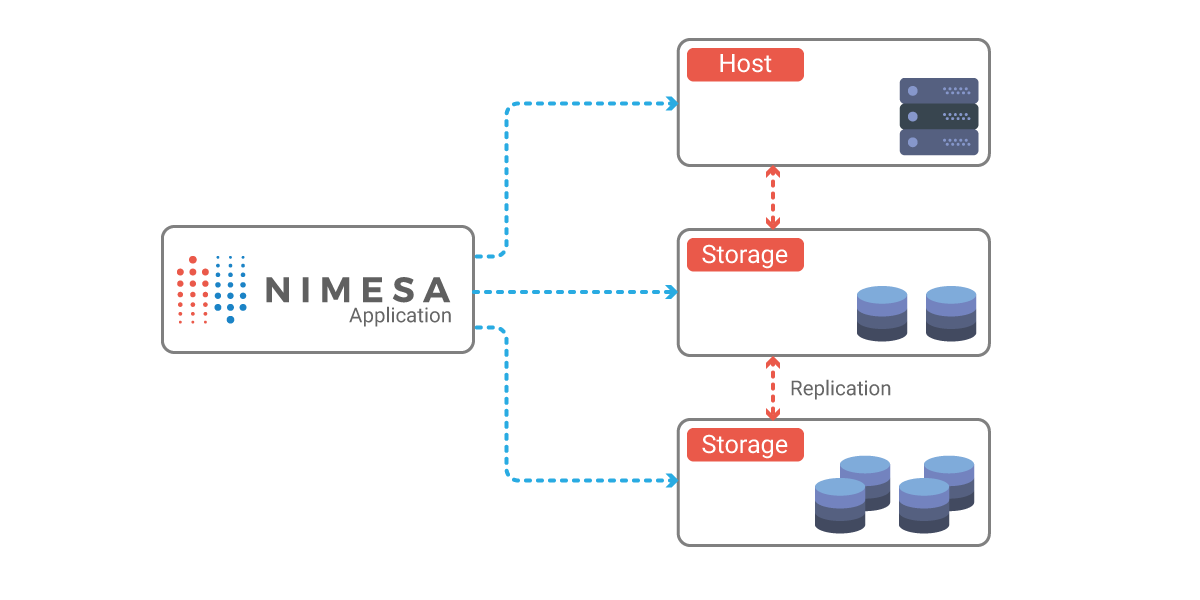
As Nimesa backups based on the snapshot (snapshots are read-only ). Nimesa helps you recover the data from the good backup copy in minutes.
Nimesa backups the Virtual Machine by taking the snapshot of the Virtual Machine and the volume of datastore ( underlying storage snapshot capabilities) in case of VMware, it creates the snapshot of the Instance volumes in case AWS cloud. In both these cases, Nimesa replicated the snapshot to another site configured by user underlying storage / AWS EBS capabilities.
In case of an attack or data loss user has the option to recover the whole machine or individual disk or even the SQL database inside the Virtual Machine. Nimesa provides data protection with smaller RPO and faster RTO.
